Tech
5 Key Steps to Identify Penetration Testing Specialists

What factors should customers take into account when turning to specialized companies, how to find real professionals for loud marketing statements, what pitfalls does this process have?
#1. Trust
How can a customer understand whether to trust this auditor company? The answer is traditional: a list of large clients and their references (open or much more often closed), how long has the company been on the market, how well known it is, etc. The issue of trust becomes a cornerstone, so qualifications are absolutely irrelevant if there is no trust.
Let’s take a closer look at the following typical problem directly related to trust – fear of pentesters. Which, in general, is correct: pentesters, like any other external consultants, should be feared. Of course, first of all, you need to be afraid … integrators and vendors who provide technical support – they are much more dangerous.
They, unlike pentesters, who know nothing but holes, are well versed in the entire system: what and where is in it and what can be done with it, besides, they have all the necessary rights. In addition, everyone has long been accustomed to integrators, and control over their activities is greatly weakened over time, which makes them even more dangerous …
Such a “hacker” team is quite difficult to manage – it takes a lot of experience, knowledge of the peculiarities, various well-built and debugged, but at the same time specific processes. It is this special experience that distinguishes mature penetration testing companies around the world, and they are trusted by top clients. Therefore, advice number 1 – use only the services of trusted, experienced and well-known specialized companies-pentesters in the market.
#2. Qualification
The second most important condition after trust is the qualification of the pentester company. The fact is that the quality of the auditors’ work is not always evidenced by the positive references of customers, since not all of them are able to objectively assess the result of the pentest carried out at their place.
What are the main objective criteria for auditor qualifications? References from customers with a high level of maturity in relation to penetration tests. References for vulnerabilities found from the world’s leading vendors (MS, Oracle, SAP, VMWare, Cisco) and web services (Google). The most objective parameter, which unambiguously indicates that the auditor company is able to look for unknown vulnerabilities in the products of serious vendors. It remains only to look at their quality and quantity.
Published research on the search for vulnerabilities (in this case, we are talking about technical research, which should not be confused with market research, which is literally teeming with the market). Speeches at the world’s leading tech hacker conferences.
Follow https://www.dataart.com/services-and-technology/security to learn more.
#3. Skill stack
- Here is a rough list of what a good pen tester need to know:
- Configure a networking stack.
- Conduct an audit of the system, analyze which place is vulnerable.
- Attack network resources in popular ways and set up a protection system against such attacks.
- Set up a monitoring system and a warning system for problems.
- Take into account the human factor in the construction of protection.
In addition, an understanding of cryptographic and other protection methods is useful. Plus, it’s good if he understands the regulatory legal acts in the field of information security, the sphere of responsibility of government agencies.
#4. Tool stack
A pentesting specialist is able to work with:
- Linux.
- Windows.
- DLP.
- IDS.
- SIEM.
- Kubernetes.
#5. Personal qualities
Pentester must be:
- sociable, be able to clearly and competently express their thoughts; stress-resistant;
- punctual;
- constantly develop, learn new tools, attend conferences;
- observe occupational hygiene so as not to burn out.
Features
Exploring Valorant eSports Stats: Unveiling the Metrics Behind Competitive Excellence
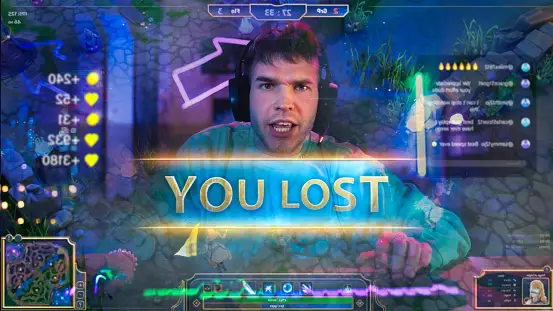
In the rapidly expanding realm of Valorant eSports, statistical analysis plays a pivotal role in understanding player performance, team dynamics, and the strategic nuances that define success in competitive play. This article delves into the significance of Valorant eSports stats, their impact on the competitive landscape, and how they empower players, teams, and fans alike.
Key Metrics in Valorant eSports Stats
Valorant eSports stats encompass a wide array of metrics that provide insights into player proficiency and team strategies. These include individual performance indicators such as kill-death ratios (K/D), average damage per round (ADR), headshot percentages, and assist counts. Team statistics such as round win percentages, first blood percentages, and economy management efficiency further illuminate strategic strengths and areas for improvement.
Analyzing Player Performance and Contribution
For professional Valorant players, statistics serve as a critical tool for evaluating individual performance and contribution to team success. By analyzing metrics like K/D ratios and ADR, players can assess their impact in securing eliminations, dealing damage, and supporting team objectives. This data-driven approach enables players to identify strengths to leverage and weaknesses to address, enhancing their overall effectiveness in competitive matches.
Strategic Insights and Adaptation
Valorant eSports stats provide valuable strategic insights that shape team tactics and gameplay adaptations. Coaches and analysts analyze statistical trends to optimize agent selections, refine map strategies, and counter opponents’ playstyles effectively. The ability to leverage data-driven decision-making empowers teams to evolve their tactics, adapt to meta-game shifts, and maintain a competitive edge in the dynamic world of Valorant eSports.
Tracking Tournament Trends and Meta-Game Evolution
Beyond individual matches, Valorant eSports stats track broader tournament trends and meta-game evolution. Historical data on agent pick rates, map preferences, and round outcomes reveal emerging strategies and meta-shifts over time. This analytical depth allows teams and analysts to anticipate trends, innovate strategies, and stay ahead of competitors in high-stakes tournaments and league play.
Fan Engagement and Spectator Experience
Valorant eSports stats enrich the spectator experience during live broadcasts and tournament coverage. Fans can follow real-time updates on player performances, compare stats across matches, and engage in discussions about standout plays and strategic decisions. Interactive platforms and statistical dashboards enhance viewer engagement, fostering a deeper connection with the competitive narratives unfolding in Valorant eSports.
Impact on eSports Betting and Fantasy Leagues
Valorant eSports stats play a crucial role in eSports betting markets and fantasy leagues, where informed decision-making hinges on statistical insights. Bettors and fantasy league participants leverage player and team stats to assess form, predict match outcomes, and manage their investments strategically. Real-time updates and comprehensive data analysis enhance the strategic depth and excitement of eSports engagement for fans worldwide.
Technological Advancements and Data Visualization
Advancements in technology have revolutionized how Valorant eSports stats are accessed and analyzed. Streaming platforms and eSports websites offer sophisticated data visualization tools, interactive heatmaps, and player performance overlays that enhance the depth and accessibility of statistical analysis. These technological innovations provide analysts, commentators, and fans with enhanced insights into gameplay dynamics and strategic decision-making.
Future Innovations in Statistic Analysis
As Valorant continues to evolve as an eSports powerhouse, the future of statistical analysis promises further innovations. AI-driven predictive analytics, enhanced machine learning algorithms, and real-time performance tracking technologies are poised to revolutionize how eSports stats are processed and utilized. These advancements will elevate the precision, depth, and predictive capabilities of statistical analysis in Valorant eSports, shaping the future of competitive gaming.
Business
Conquer the Digital Toolbox: A Home Improvement Pro’s Guide to Online Marketing Success

In the not-so-distant past, home improvement businesses thrived on word-of-mouth referrals and the occasional ad in the local newspaper. But times have changed. Today’s homeowners are tech-savvy, turning to their smartphones and laptops to research contractors, compare prices, and read online reviews before making a decision. This shift towards digital means that even the smallest mom-and-pop operation needs a strong online presence to stay competitive.
The good news is, the internet has leveled the playing field. It’s no longer about who has the biggest advertising budget; it’s about who has the smartest digital marketing strategy. By understanding the fundamentals of search engine optimization (SEO) and implementing effective online marketing tactics, even small businesses can punch above their weight and attract a steady stream of qualified leads.
Building Your Online Basecamp
Utilizing home improvement SEO strategies might sound like a complex digital puzzle, but it boils down to a simple goal: making sure your business pops up when potential customers search for the services you offer. Imagine a homeowner in your area with a leaky pipe. What are they most likely to do? Grab their smartphone and search for “plumber near me” or “emergency plumbing services”. If your website isn’t optimized for these types of searches, you’re essentially invisible to those customers who are actively seeking your help.
This is why SEO is so crucial for home improvement businesses. Homeowners facing a plumbing issue, a damaged roof, or a pest infestation don’t have the luxury of browsing through endless pages of search results. They need immediate solutions, and your website needs to be at the top of those results to capture their attention.
Regardless of your specific trade, there are some foundational SEO steps that every home improvement business should take. Start by claiming and optimizing your Google Business Profile (formerly Google My Business). This free listing allows you to manage how your business appears in Google searches and Maps, ensuring potential customers have accurate contact information and hours of operation.
Consistency is key: make sure your business name, address, and phone number are consistent across all online platforms, from your website to your social media profiles. This builds credibility and makes it easier for search engines to associate your business with relevant search terms.
The HVAC Pro’s Digital Tune-Up
Ready to crank up your HVAC business’s online presence? The key is to start with a focused and actionable plan. Forming a helpful HVAC digital marketing checklist to do right now can be your first step towards success, guiding you through the essential stages to boost your visibility and attract more customers.
Begin by targeting the right keywords. Generic terms like “furnace repair” or “air conditioning” are highly competitive. Instead, get specific to your service area and offerings. Think “emergency furnace repair in [your city]” or “AC tune-up specials in [your neighborhood].” By tailoring your keywords to the searches potential customers in your area are actually conducting, you increase the chances of your website appearing at the top of relevant results.
Content marketing plays a crucial role in establishing your expertise and building trust. Think of your website’s blog as an opportunity to answer common questions before customers even pick up the phone. Craft informative articles or videos on topics like “How to Choose the Right Air Filter for Your Home” or “5 Signs Your AC Needs Repair.” By offering valuable advice, you not only attract potential customers through search engines but also position yourself as a knowledgeable resource.
Don’t underestimate the power of social media for HVAC businesses. Platforms like YouTube and Facebook can be powerful tools for showcasing your expertise and connecting with your community. Consider creating short “how-to” videos on simple maintenance tasks, sharing before-and-after photos of your projects, or even offering virtual consultations to answer questions and address concerns. By being active and engaged on social media, you can build brand awareness and trust, which ultimately translates into more leads and higher conversion rates.
Roofing Marketing: Beyond the ‘After’ Photo
While impressive before-and-after photos of completed projects remain actual in roofing marketing ideas, the digital age demands a more nuanced approach. While those shiny new roofs might capture initial attention, they don’t tell the whole story. To truly connect with potential clients and differentiate your company from the competition, you need to delve deeper.
Sharing compelling case studies that showcase your expertise and problem-solving skills can be incredibly impactful. Highlighting unique challenges you’ve encountered, such as intricate roof designs or unusual materials, demonstrates your capabilities and reassures potential clients that you can handle their specific needs. Client testimonials add another layer of authenticity to your marketing efforts. Allowing satisfied customers to share their positive experiences in their own words builds trust and credibility.
Partnering with local real estate agents can be a mutually beneficial strategy. They often encounter homeowners who need roof repairs or replacements, and your expertise can be a valuable asset to their clients. By offering referral incentives or even co-hosting informational webinars, you can forge strong relationships within your community and gain access to a steady stream of qualified leads.
Finally, don’t underestimate the power of local SEO. Optimizing your website for keywords like “roofers near me” or “roofing companies in [your city]” ensures that your business appears prominently in search results when homeowners in your area are actively seeking roofing services.
The Pest Control Playbook
Pest control isn’t a year-round concern for most homeowners, which means learning about specifics of pest control SEO is required for successful marketing. Searches for “pest control” services often spike during specific seasons. Think about it: you’re more likely to worry about tick prevention in the spring, mosquito control in the summer, and mice infestations as the weather turns cold. Understanding these seasonal trends is crucial for tailoring your content to address the most pressing concerns of potential customers at any given time.
For many people, dealing with a pest infestation is an emotional experience. It can trigger feelings of anxiety, disgust, and even fear. This is where content marketing plays a crucial role in not just attracting clients, but reassuring them. Instead of solely focusing on advertising your extermination services, offer helpful information that empowers homeowners to take preventive measures. Blog posts on identifying common pests, tips for keeping rodents out of your home, or natural remedies for insect control show you understand their concerns and are invested in their well-being.
In the pest control industry, online reviews are worth their weight in gold. When dealing with an infestation, people want fast, effective solutions. Positive reviews on platforms like Google and Yelp build trust quickly, assuring potential customers that your company has a proven track record of success.
Measuring Your Wins
It’s tempting to measure your digital marketing success by the number of likes, shares, or followers you accumulate on social media. While these “vanity metrics” might feel good, they don’t necessarily translate into real business growth. For home improvement companies, the true measure of success is the number of qualified leads and booked jobs generated by your online efforts.
Don’t get lost in a sea of clicks and impressions. Instead, focus on tracking the metrics that truly matter to your bottom line. How many visitors to your website actually fill out your contact form or call to schedule an estimate? How many of those leads turn into paying customers? By carefully tracking these conversions, you can gain valuable insights into which marketing channels are most effective, which types of content resonate with your audience, and ultimately, what’s driving your business forward.
While the world of website analytics can be intimidating, there are user-friendly tools available to help you track your progress without getting bogged down in technical details. Google Analytics, for example, provides a wealth of information about your website traffic, including where visitors are coming from, which pages they’re viewing, and how long they’re staying on your site. By setting up conversion tracking, you can even see which marketing efforts are directly resulting in leads and sales. Other platforms offer simplified dashboards and reports tailored to the needs of small businesses, making it easier than ever to harness the power of data and make informed decisions about your marketing strategy.
When to Get Expert Help
While the initial stages of home improvement SEO can be handled in-house, there comes a point when seeking professional guidance becomes a wise investment. If you’ve diligently implemented the basic steps of SEO, like optimizing your website and Google Business Profile, but aren’t seeing the desired results, don’t despair. It could simply mean your business needs a more comprehensive and tailored approach. Similarly, if the thought of managing a blog, crafting social media posts, or analyzing complex website data makes you want to pull your hair out, it’s okay to admit you need help.
When searching for a marketing partner, it’s crucial to find an agency with a deep understanding of the unique challenges and opportunities faced by home improvement businesses. A generic marketing agency might have experience with e-commerce or retail, but they won’t grasp the nuances of the construction industry. Look for a company that specializes in home services marketing. They’ll understand the seasonal fluctuations in demand, the importance of local SEO, and the specific types of content that resonate with homeowners.
Conclusion: Building Your Digital Empire
Building a powerful online presence for your home improvement business is a journey, not a destination. SEO isn’t a magic wand you wave once to achieve instant success. It’s an ongoing process that requires patience, consistent effort, and a willingness to adapt to the ever-changing digital landscape. But the rewards are well worth the investment. By staying committed to your SEO strategy, you can steadily climb the search engine rankings, attract a consistent flow of qualified leads, and establish your business as a trusted authority in your local market. Don’t be afraid to seek out additional resources and guidance as you navigate this digital journey. There are several industry-specific blogs and podcasts that offer valuable insights and advice on how to optimize your online presence. Resources like Comrade Digital Marketing blog can help you stay up-to-date on the latest trends, learn from the successes (and failures) of others, and ultimately build a thriving online empire that sets your home improvement business apart from the competition.
Business
Exploring the Steps in the Proposal Automation Process

In a fast-paced business environment, efficiency is key to staying ahead of the competition. Proposal automation offers a strategic advantage by streamlining the creation of documents that are vital to winning new business. By automating routine tasks, companies can focus more on the substance and strategy of their proposals. Understanding how it works and the significant improvements it can bring to your business operations is essential. Below, we delve into this process and discuss everything you need to know about optimizing your proposal automation process.
Understanding the Foundation of Proposal Automation
At its core, proposal automation is about enhancing productivity and consistency within the process of creating proposals. By leveraging technology, it replaces the traditional, manual method of drafting documents with a more streamlined, error-proof approach. This transition includes the use of templates, content libraries, and customized data inputs to ensure each proposal is tailored, yet produced with greater speed and accuracy.
For newcomers, understanding the foundation is crucial before implementation. This involves grasping the basics of how automated systems manage data, apply business logic, and produce finalized documents. It’s essential to ensure that your team is well-versed with the system and that all relevant content is digitized and made accessible to the automation software.
Key Benefits of Implementing Proposal Automation
Proposal automation systems offer a multitude of benefits, the most prominent being the drastic reduction in time spent drafting proposals. Employees are freed from repetitive formatting tasks, allowing them to devote more time to strategic functions such as market analysis and personalized client engagement which can significantly influence the success of a proposal.
Error reduction is another major advantage of automating the proposal process. With standardized templates and centralized content management, inconsistencies are minimized, and the risk of outdated information being included is significantly reduced. This elevates the professionalism and credibility of each proposal generated.
Essential Features to Look for in Proposal Automation Tools
Choosing the right proposal automation tools is essential for achieving the desired efficiency and effectiveness. The most valuable feature to look for in such a tool is a robust content library. This allows for quick access to the most current and relevant pieces of content and data necessary for crafting a compelling proposal.
Integration capability is another crucial feature. The tool should be able to integrate seamlessly into the existing technology ecosystem of your organization, including CRM platforms, to facilitate smooth workflows and information exchange. This ensures that sales and proposal teams work with the latest client information and reduce duplication of efforts.
Step-by-Step Guide to the Proposal Automation Workflow
The journey of automating your proposal process starts with the initial setup of the proposal automation tool. This involves configuring the system with your company’s templates, content, and workflows. A key aspect here is to ensure that the templates accommodate various proposal scenarios and that the content library is organized and tagged for easy retrieval.
Next, the tool is integrated with other enterprise systems such as CRM software, ensuring that data flows continuously and accurately between platforms. This step is crucial for maintaining up-to-date content in the proposals and for personalizing them with client-specific data.
Measuring Success and ROI in Proposal Automation Initiatives
To truly understand the impact of proposal automation, it’s important to measure its success and return on investment (ROI). One of the most straightforward metrics to monitor is the reduction in the time required to generate proposals. Noticing a considerable decrease here is often the first sign that the automation is effective.
Another valuable indicator is the quality and consistency of proposals. With fewer errors and greater adherence to company branding, the professionalism conveyed in each proposal can lead to better client perceptions and a higher win rate. Monitoring feedback and win rates can give concrete evidence of the system’s effectiveness.
-

 Guides4 years ago
Guides4 years ago6 Proven Ways to Get more Instagram Likes on your Business Account
-

 Mainstream9 years ago
Mainstream9 years agoBioWare: Mass Effect 4 to Benefit From Dropping Last-Gen, Will Not Share Template With Dragon Age: Inquisition
-

 Casual8 months ago
Casual8 months ago8 Ways to Fix Over-Extrusion and Under-Extrusion in 3D Printing
-

 Guides5 months ago
Guides5 months agoExplore 15 Most Popular Poki Games
-

 Guides1 year ago
Guides1 year agoGan Rubik’s Cube vs. Traditional Rubik’s Cube: Key Differences and Advantages
-

 Uncategorized3 years ago
Uncategorized3 years agoTips To Compose a Technical Essay
-

 iOS Games1 year ago
iOS Games1 year agoThe Benefits of Mobile Apps for Gaming: How They Enhance the Gaming Experience
-

 Mainstream11 years ago
Mainstream11 years agoGuild Wars 2: The eSports Dream and the sPvP Tragedy
